Using a SOCKS proxy allows you to encrypt all your web traffic between your machine and the proxy server, making it impossible for any local devices to inspect your traffic. Besides the obvious use-cases, this can often mean a significant impact on your browsing speed as it allows your traffic to exit from a different geographical location.
Prerequisites
Whether or not you can use a SOCKS proxy is highly dependent on your environment: is this a home PC behind a simple router, a work computer behind the corporate firewall or your school issued laptop on a public WiFi? There are three basic things you need:
- The ability to run PuTTY
- Connectivity to the internet that is not inspected by any “smart” devices
- A server with shell access (SSH) enabled
To check if you can run PuTTY, simply download “putty.exe” from the official PuTTY download page (direct link to putty.exe) and run it. If you do not get an error: great! If Applocker prevents you from running it, you might get stuck here. This is often deployed on corporate devices.
In corporate environments typically internet connectivity is impossible except from the corporate proxy to the outside. To test this, you’ll need to run PuTTY and see if you can open a SSH session to your server, use following settings:
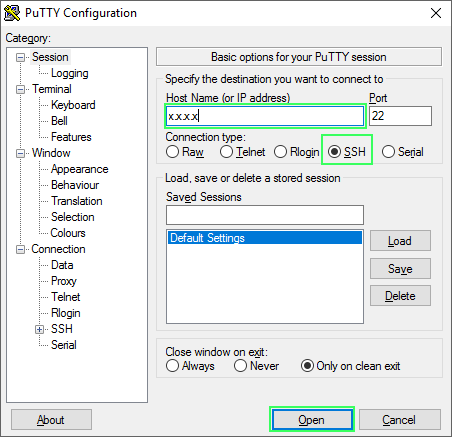
If you get a warning about a private key or password prompt you have everything you need to setup a SOCKS tunnel.
Configuring PuTTY
Navigate to Connection -> SSH -> Tunnels and do the following:
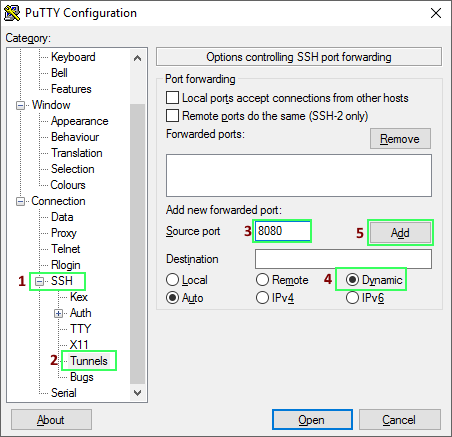
Instead of 8080 you can type in any local port, but higher port numbers (>1023) are required as the lower ports require administrative access. After this step, go back to Session and do the following:
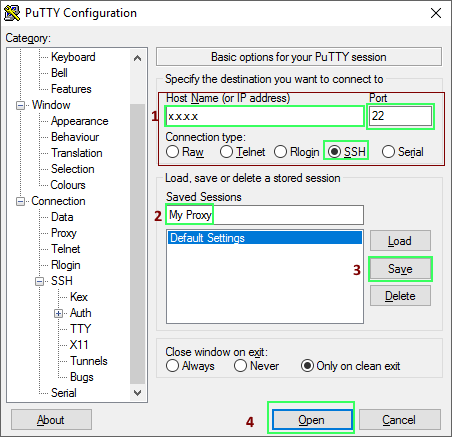
Saving the session is useful so you don’t have to do this every time you open up PuTTY. Click Open and log in into your server. Now go to your browser and change the proxy settings to use the SOCKS proxy. In Firefox:
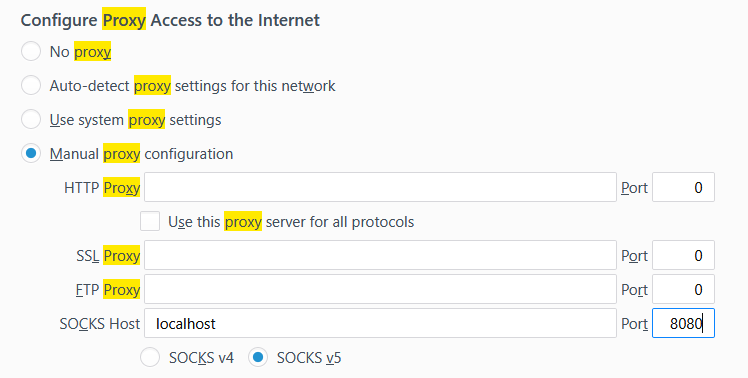
Don’t forget to change the 8080 if you changed it in the previous step.
Testing the proxy
Go to one of the million “what is my IP?” websites, it should show the IP from your server.
Advanced tips
Often corporate networks don’t allow port 22 going out, so you can change the config on your server to listen on a different port. To do this (on 99% of Linux installations at least) open a CLI window and edit the /etc/ssh/sshd_config config file, add following lines:
Port 22
Port 10022
Change the port 10022 to any port you find to be open. After this restart sshd:
systemctl restart sshd.service
You can also try to be clever and use a less conspicuous port such as 443, but these are often subject to protocol detection on a firewall. This means you won’t be able to get any SSH traffic over them, only actual HTTPS traffic.

Leave a Reply